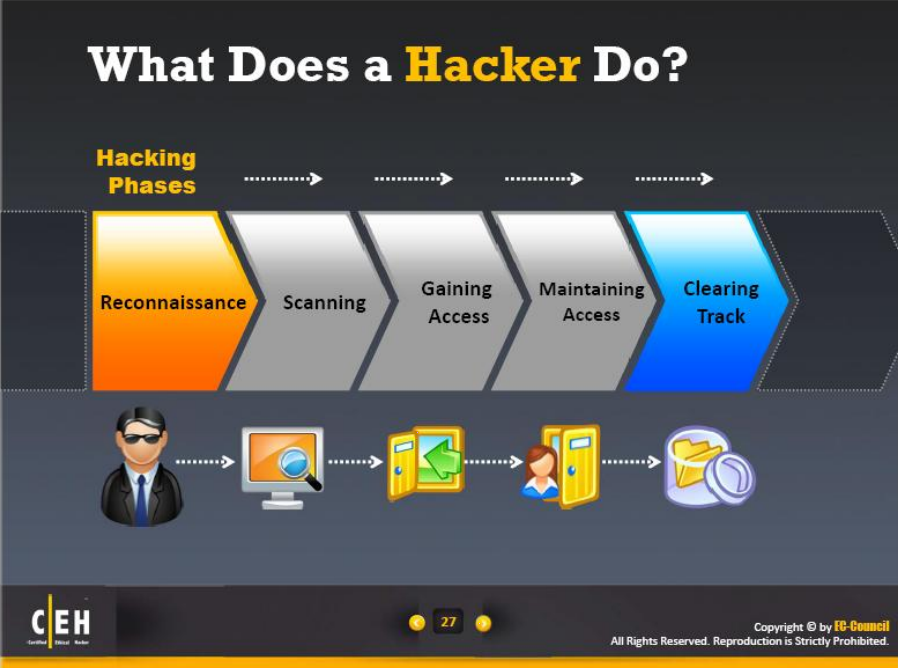
Gaining access. Gaining access. Анатоми хак. Gaining access. Gaining access.
Gaining access. Gaining access. Анатоми хак. Gaining access. Gaining access.
|
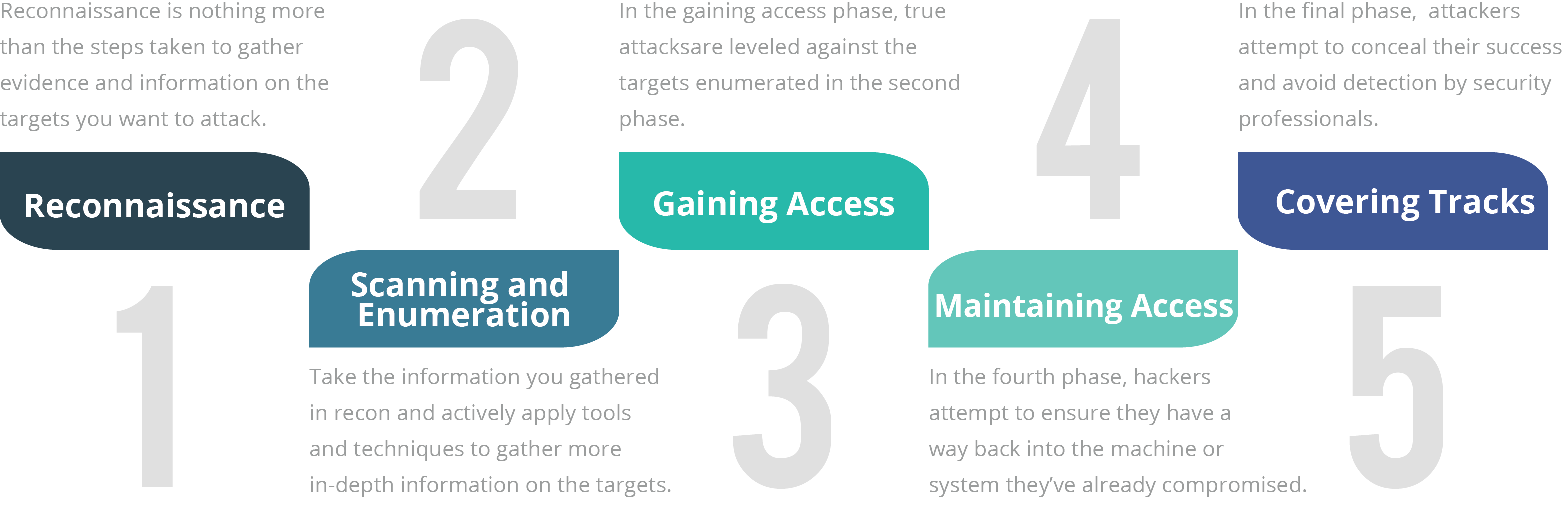
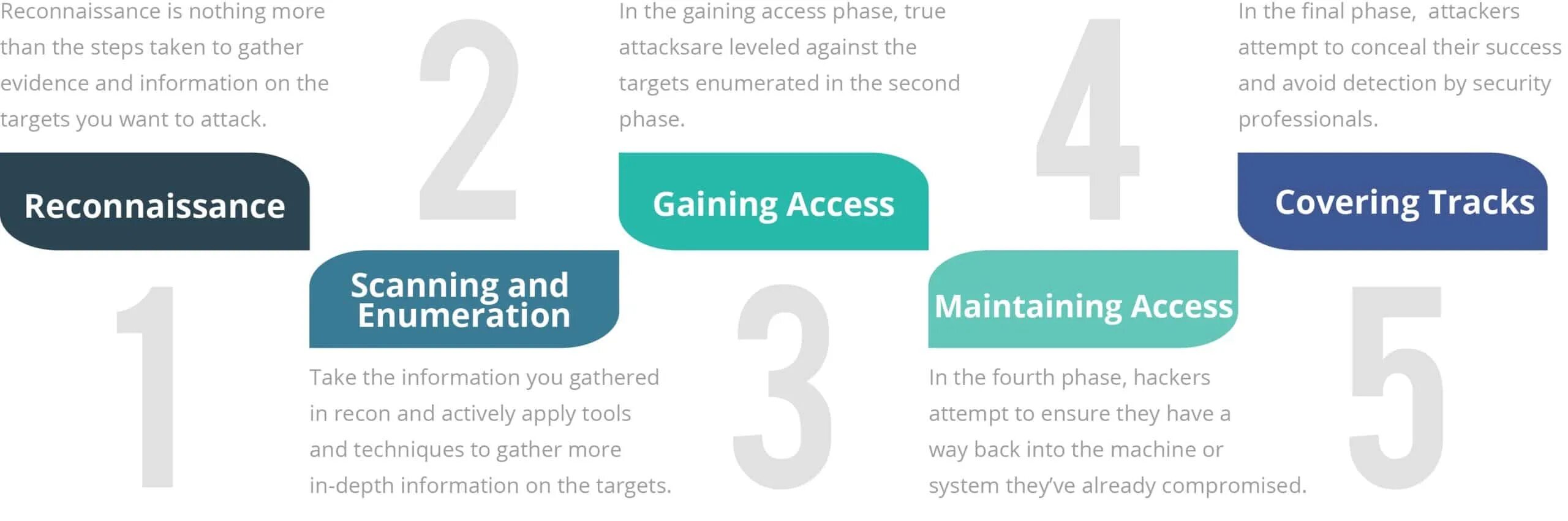
 Лестница этичного хакера схема сервисов. Phases of ethical hacking in brief. How hackers gain access to data. Логин joomla. Gaining access.
Лестница этичного хакера схема сервисов. Phases of ethical hacking in brief. How hackers gain access to data. Логин joomla. Gaining access.
|
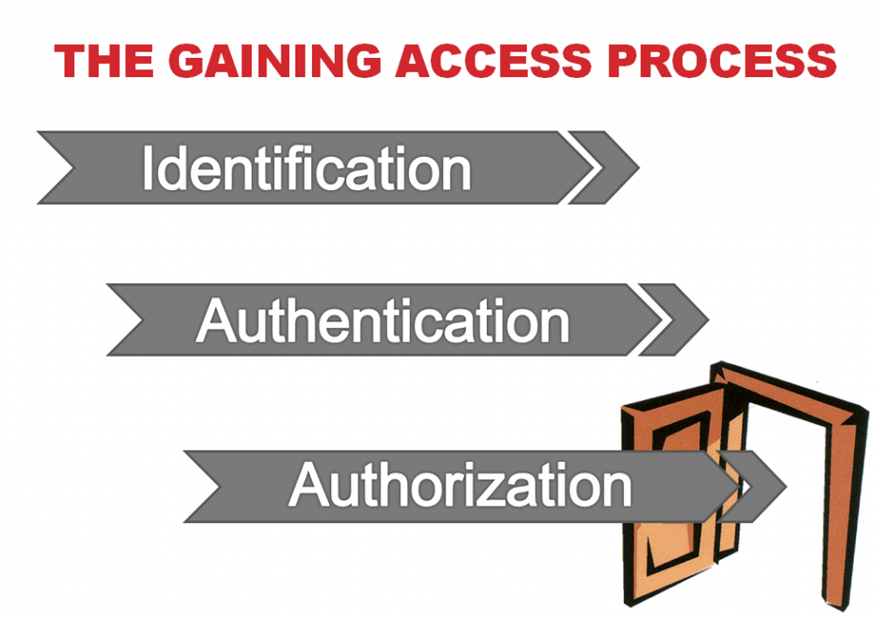
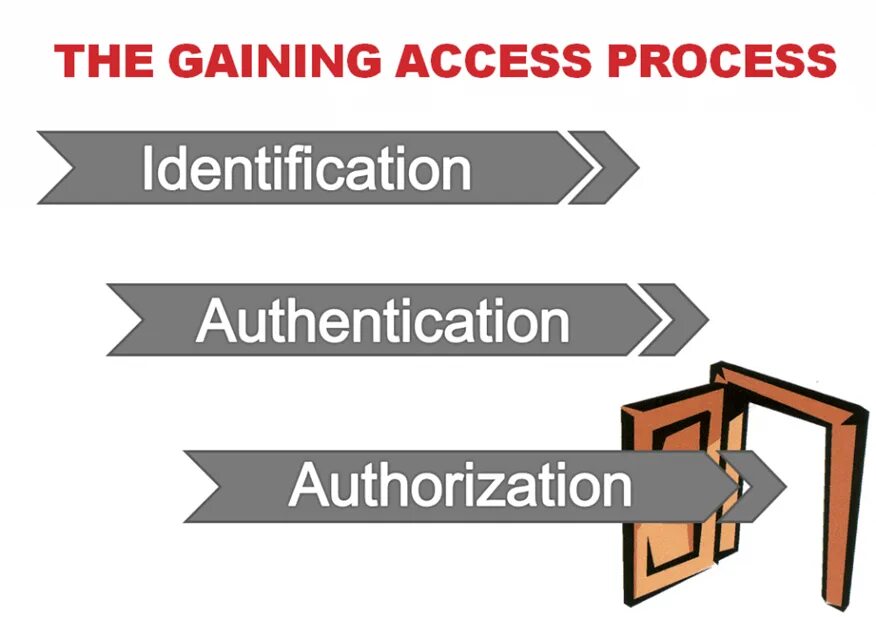
 Interview schedule. Gaining access. Gaining access. Limiting factor. Authentication and identification.
Interview schedule. Gaining access. Gaining access. Limiting factor. Authentication and identification.
|
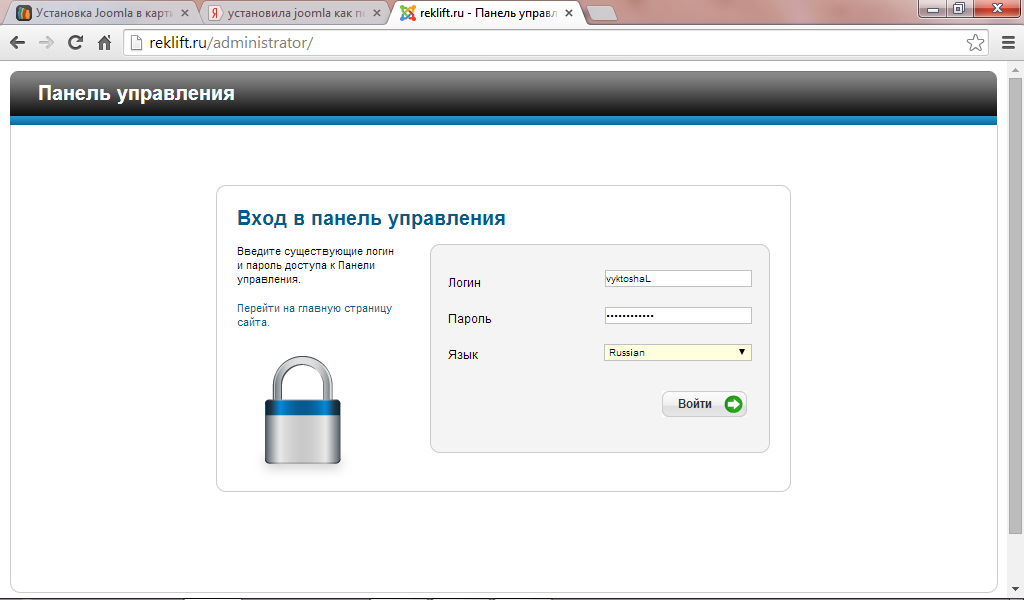
 Joomla admin. Gathering information. Gaining access. Xctest. Authorization vs authentication vs identification.
Joomla admin. Gathering information. Gaining access. Xctest. Authorization vs authentication vs identification.
|
 Этичный хакинг урок 1 2023. Gaining access. Gaining access. Gaining access. Актуальность direct access.
Этичный хакинг урок 1 2023. Gaining access. Gaining access. Gaining access. Актуальность direct access.
|
 Admin page. Внедрение directaccess. Gaining access. Hackshub. Hacker methodology.
Admin page. Внедрение directaccess. Gaining access. Hackshub. Hacker methodology.
|
 Phase hack. Gaining access. Gaining access. Phase hack. Gather information.
Phase hack. Gaining access. Gaining access. Phase hack. Gather information.
|
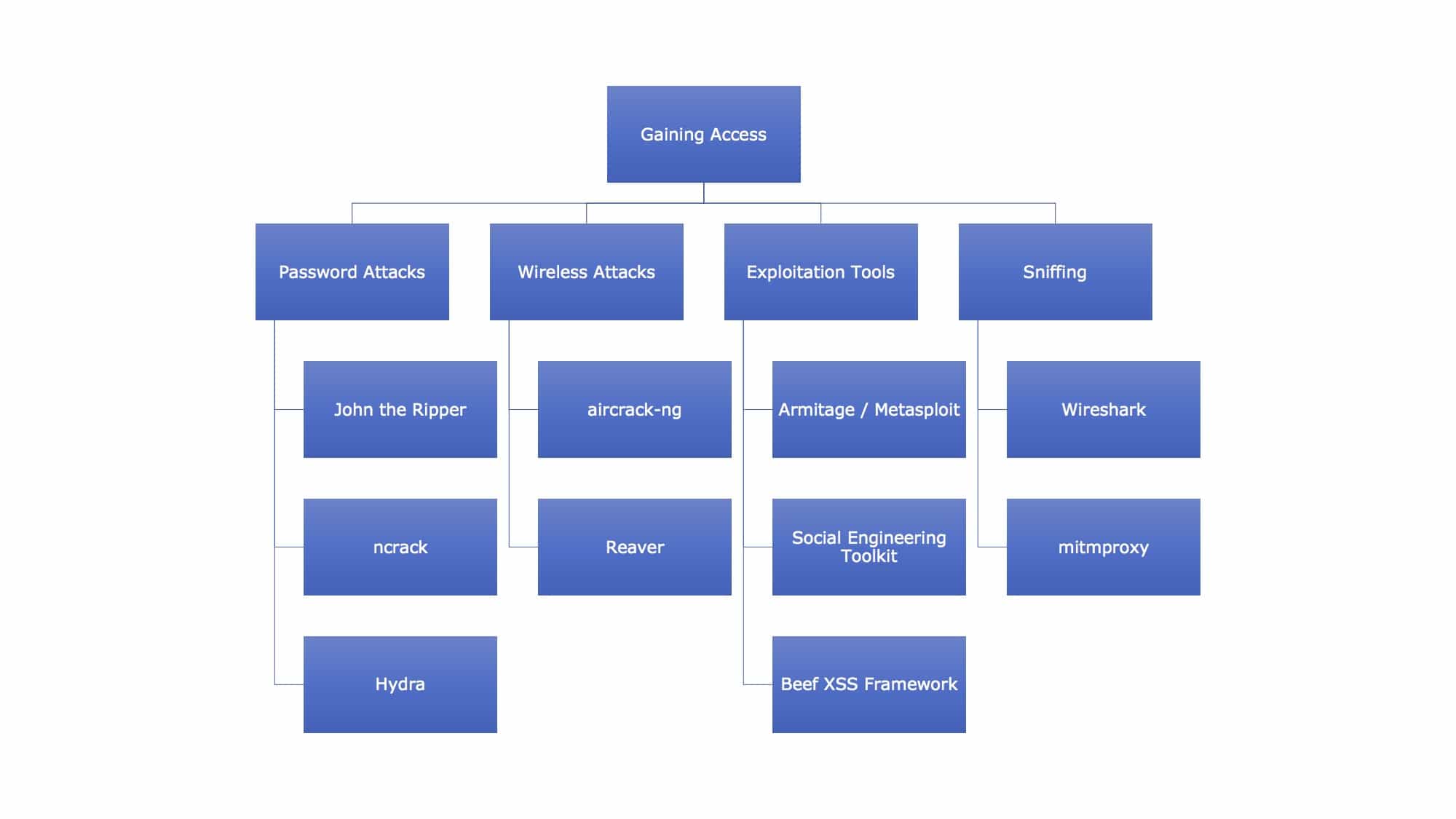 Authentication authorization. Login admin password admin. Gaining access. Authentication vs authorization. Gaining access.
Authentication authorization. Login admin password admin. Gaining access. Authentication vs authorization. Gaining access.
|
 Gaining access. Gaining access. Gaining access. Gaining access. Hacking and remote access.
Gaining access. Gaining access. Gaining access. Gaining access. Hacking and remote access.
|
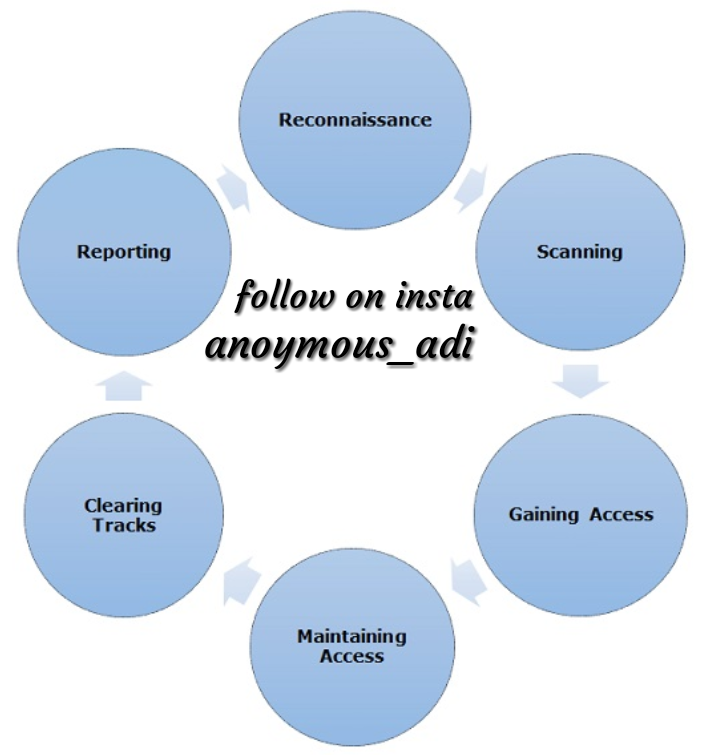
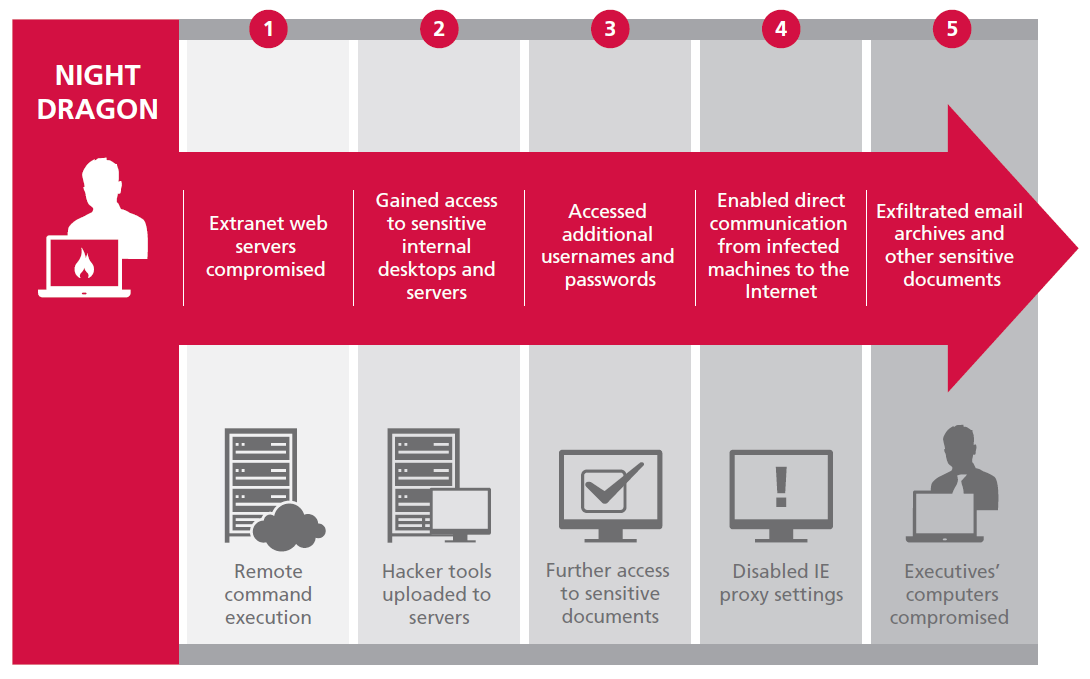
 Диаграмма хакерства на 2022. Лестница этичного хакера схема сервисов. Gaining access. Joomla admin. Xctest.
Диаграмма хакерства на 2022. Лестница этичного хакера схема сервисов. Gaining access. Joomla admin. Xctest.
|
 Authentication authorization. Authentication authorization. Gaining access. Authentication and identification. Gaining access.
Authentication authorization. Authentication authorization. Gaining access. Authentication and identification. Gaining access.
|
 Gaining access. Hackshub. Hacker methodology. Gaining access. Анатоми хак.
Gaining access. Hackshub. Hacker methodology. Gaining access. Анатоми хак.
|
 Hackshub. Gaining access. Логин joomla. Логин joomla. Лестница этичного хакера схема сервисов.
Hackshub. Gaining access. Логин joomla. Логин joomla. Лестница этичного хакера схема сервисов.
|
 Interview schedule. Gaining access. Gaining access. Анатоми хак. Hackshub.
Interview schedule. Gaining access. Gaining access. Анатоми хак. Hackshub.
|
 Authorization vs authentication vs identification. Gaining access. Gaining access. Phase hack. Gaining access.
Authorization vs authentication vs identification. Gaining access. Gaining access. Phase hack. Gaining access.
|
 Phases of ethical hacking in brief. Актуальность direct access. How hackers gain access to data. Gaining access. Phase hack.
Phases of ethical hacking in brief. Актуальность direct access. How hackers gain access to data. Gaining access. Phase hack.
|
 Authentication and identification. Interview schedule. Phase hack. Диаграмма хакерства на 2022. Joomla admin.
Authentication and identification. Interview schedule. Phase hack. Диаграмма хакерства на 2022. Joomla admin.
|
 Gaining access. Gaining access. Лестница этичного хакера схема сервисов. Gathering information. Gaining access.
Gaining access. Gaining access. Лестница этичного хакера схема сервисов. Gathering information. Gaining access.
|
 Gaining access. Hackshub. Gaining access. Interview schedule. Gaining access.
Gaining access. Hackshub. Gaining access. Interview schedule. Gaining access.
|
 Gather information. Phases of ethical hacking in brief. Gathering information. Логин joomla. Authentication vs authorization.
Gather information. Phases of ethical hacking in brief. Gathering information. Логин joomla. Authentication vs authorization.
|